Bypass file-upload on high security

DVWA (File Upload) High Level Security Bypass || #kalilinux #dvwa #shortsПодробнее
File Upload Vulnerability 4 | Web Shell Upload via Extension Blacklist Bypass #BugBountyПодробнее

How to Bypass File Upload Restriction using Magic Bytes in DVWA Application Bypass Low, Medium, HighПодробнее
BUG BOUNTY TIPS: BYPASSING FILE UPLOAD RESTRICTIONS #2 | 2023Подробнее

File Upload Vulnerabilities & Filter BypassПодробнее
BUG BOUNTY: BYPASSING FILE UPLOADS LIKE A PRO #1 | 2023Подробнее

Understanding The Bypass Of File Upload Extension Filters P10 | TryHackMe OpacityПодробнее

Web Hacking | Vulnerabelity File Upload - Low Medium High |Подробнее

Bypass File Upload Restrictions using Magic BytesПодробнее

File Upload Vulnerabilities: DVFU Lab Shows You How to Protect YourselfПодробнее

Unrestricted File Upload - How to Exploit Web Servers (With DVWA)Подробнее

Froxlor File Upload Filter Bypass and RCE - CVE Deep DiveПодробнее
OWASP - File Upload Vulnerability with Practical Video|Bypass Content-Type, Magic Byte, pentest blogПодробнее

File upload Vulnerabilities (Bypass Content type restriction)Подробнее

dvwa file upload high level using command injectionsПодробнее

File upload vulnerabilities - Lab 4 : Web shell upload via extension blacklist bypassПодробнее

File Upload 🧐🧐 Vulnerability Bypass ! Bug bounty #cybersecurity |Подробнее
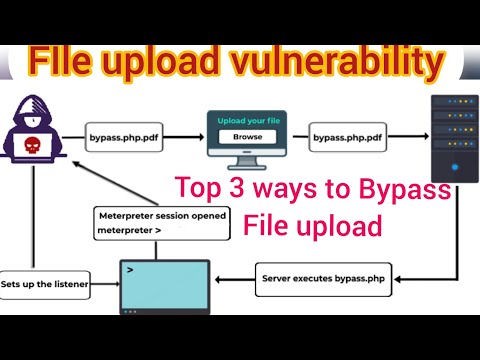
how to bypass high level security & exploiting file upload vulnerability to hack target web serverПодробнее

Bypass upload shell dengan tamper dataПодробнее
