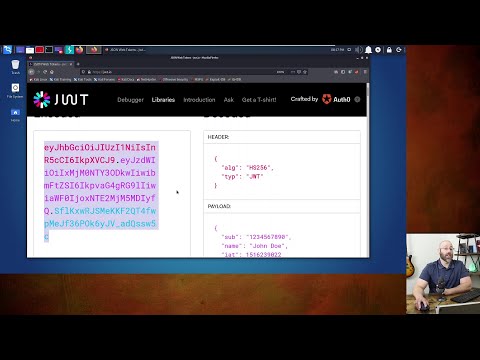
Hacking and Securing JSON Web Tokens(JWT) - Manually creating HS256 signature

Hack JWT using JSON Web Tokens Attacker BurpSuite extensionsПодробнее
Hacking and Securing JSON Web Tokens(JWT) - None signature attackПодробнее

JSON Web Token HackingПодробнее
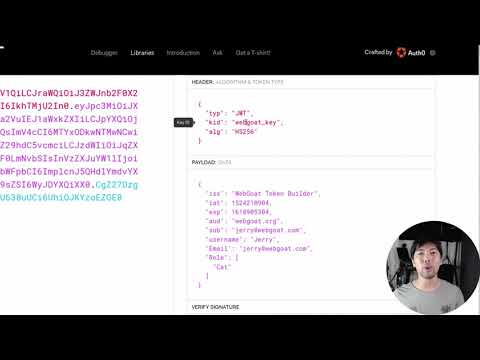
Cracking JSON Web TokensПодробнее

How to Exploit "Json Web Token"(JWT) vulnerabilities | Full PracticalПодробнее

Hacking and Securing JSON Web Tokens(JWT) - Course IntroductionПодробнее

Hacking JWT | Accepting tokens with no signatureПодробнее

JWT Hacking (JSON Web Token)Подробнее

JWT HS256Подробнее

HS256 vs RS256 with JSON Web Tokens (JWTs)Подробнее

5 JWT Signature With HS256 How Does It Work Learn What is an HMAC CodeПодробнее

Understanding JWT Authentication Fast! 🚀Подробнее

what is jwt token authentication | attacking jwt for beginnersПодробнее

The magic of JSON Web Tokens (JWT)Подробнее

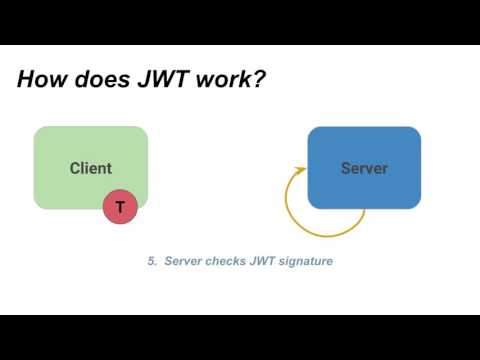
How does JWT workПодробнее
Hacking JSON Web Tokens - Ben DechraiПодробнее

The Hacker's Guide to JWT SecurityПодробнее

Don’t Use JWT for Login SessionsПодробнее
Intro to JWT VulnerabilitiesПодробнее