Top Cybersecurity Expert Reveals Essential Port Forwarding Techniques!

What The Heck Is Port Forwarding?Подробнее

Top Cybersecurity Expert Reveals Zero Trust Security SecretsПодробнее

Top Cybersecurity Expert Reveals Social Media Data Secrets!Подробнее

Top Cybersecurity Expert REVEALS Software & Server BEST PracticesПодробнее

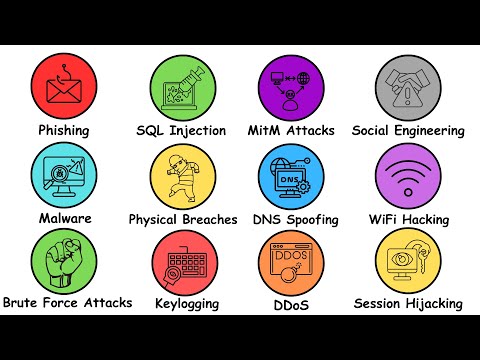
Every Hacking Technique Explained As FAST As Possible!Подробнее

CYBERSECURITY EXPERT Reveals Top Audit Techniques for 2024!Подробнее

Top 6 Types of Ethical Hacking Explained | Essential Techniques for Cybersecurity | AdaptvidsПодробнее

4 FREE Port Forwarding Tools For Hackers! (How to use them?) - Full GuideПодробнее

You ever seen these devices? Networking for Hackers and Cybersecurity professionals.Подробнее

Networking Basics For Ethical Hackers: Protocols & PortsПодробнее

Cosplay by b.tech final year at IIT KharagpurПодробнее

Port Forwarding ExplainedПодробнее

6 Must-Have Security Gadgets That Fit in Your PocketПодробнее

Port Forwarding Easily ExplainedПодробнее

My Top 5 SSH Techniques, Tips, and Tricks. Port Forwarding, Session sharing and more..Подробнее

Credentials in configs are dangerous!Подробнее

Every Hacking Technique Explained in 4 MinutesПодробнее